Authored by Shawn Ranjbaran, Principal and Ali Wasti, Managing Director, Hewlett Packard Pathfinder

The need to operate securely in hybrid and multi-cloud environments has been a significant driver in the evolution of cybersecurity. To add to this, Generative AI (GenAI) has expanded the attack surface in profound new ways, ushering the need for new “AI Security” solutions. As we prioritize both hybrid enterprise and AI offerings, securing applications, identities, data, and endpoints becomes ever more challenging. To that end, Hewlett Packard Pathfinder continues to closely follow the cybersecurity landscape, segment the market, identify key themes, and make investments where it sees strategic value.
The cybersecurity landscape is evolving due to a variety of trends in the enterprise workplace. These trends include changes in how end users work such as the rise of hybrid work environments and the subsequent expansion of potential security vulnerabilities. Additionally, security organizations are increasingly adopting Zero Trust architectures, focusing more on security within the software development lifecycle, and dealing with a scarcity of cybersecurity professionals. These movements are shaping the way we classify sectors within the cybersecurity field. We will explore these themes in more detail below.
Migration to the Cloud will continue to drive a decentralized network security approach and the need to secure all devices, across all applications. As such, this trend aims to replace the traditional network model focused on a static security perimeter in favor of secular trends. Corroborating this notion, analysts estimate that by 2025 over 95% of new digital workloads will be deployed on cloud-native platforms, up from 30% in 2021.¹
Zero Trust and Secure Access Service Edge (SASE) architectures (explained below) are implemented to continuously authenticate and authorize identities. Enterprises modernizing with Zero Trust and SASE believe connectivity and security should focus on identity and devices rather than a datacenter-focused architecture.
“Shift-Left”, a software development approach used by DevOps/DevSecOps, emphasizes the early implementation of security into the application development lifecycle. Two of the most prevalent Shift-Left practices are Software Supply Chain security, which involves securing the use of open-source and third-party software, and API Security. Evidencing the latter, Gartner found that ~90% of web apps have a greater attack surface via their APIs than UIs.
Attack surfaces continue to grow due to hybrid work, open-source/third-party software, and emerging technologies. Typically, Cloud/Application Security Posture Management (CASB, ASPM) solutions are used to address many of the related risks by monitoring behaviors, explaining dependencies, and prioritizing vulnerabilities. However, GenAI has raised the bar. Acting as a double-edge sword, GenAI can, on one hand, arm security professionals with the ability to anticipate threats by generating simulated attacks, and on the other, GenAI can enable cybercriminals to develop malicious, polymorphic code that evades detection or deepfakes that outsmart authentication systems.
Cybersecurity demand is outpacing talent. A recent study by ISC2, an international cybersecurity member association, indicated that the gap between global demand and cyber workforce capacity in 2022 was estimated at 3.4 million people, a 26% increase over the previous year.² As a result, the talent shortage has boosted the demand for managed security services and easily adoptable, low-code/no-code solutions. “Managed services” are accomplished by human operators enabled by proprietary and third-party software and include tasks such as cloud security monitoring, detection and response, and exposure management. Reflecting this trend, a recent PWC global survey found that “more than 2/3 of top performing companies use managed services for strategic advantage or to close capability gaps.”³
Each aforementioned theme has driven our interest in one or more subsectors within cybersecurity. The expansion of cloud-based platforms, remote workforces, and the Software as a Service model is transforming the structure of corporate networks. Organizations are now tasked with securing a wide array of devices and safeguarding data stored on cloud services, which lies beyond the confines of the conventional network boundaries.
In response to these challenges, Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA) models have emerged to enhance network and cloud security. ZTNA and SASE, in combination, help secure Identity and Access for the modern enterprise. “Shift-Left” has expanded our focus on Application Security in the context of application development, specifically ASPM (Application Security Posture Management). The growing attack surface, owing especially to the malicious use of GenAI, is ushering in a new category of AI Security solutions (more on this later). Finally, Security Operations companies, which offer (semi)automated and/or fully-managed solutions (e.g., Managed Detection & Response) continue to be of importance with less technical and hands-off enterprises that want a solution but may not need granular controls or have inhouse IT staff to manage the more sophisticated solutions.
Our view of the market is synthesized in Pathfinder’s high-level Cybersecurity Landscape below. (This contains representative private companies for each category and is not meant to be a comprehensive list).
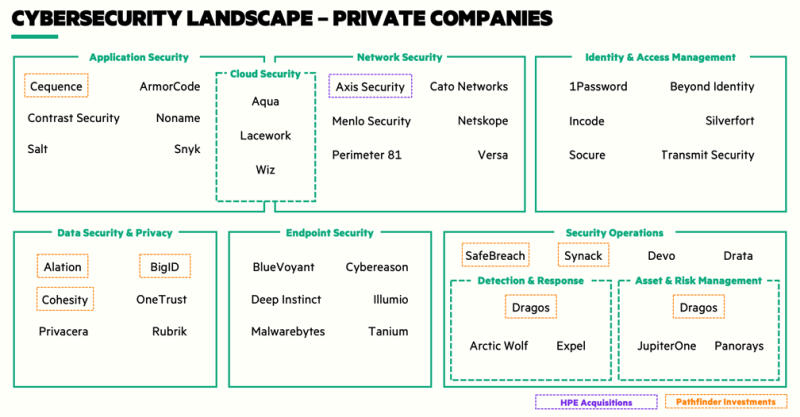
Cybersecurity Subsectors – To get a better understanding of each of these sectors within Cybersecurity, below is a brief description and key concepts.
• Network Security: Network security providers are adapting to the cloud-driven landscape by focusing on Secure Access Service Edge (SASE) frameworks. Recognizing this, HPE acquired Axis Security, which provides Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), and a Cloud Access Security Broker (CASB) – altogether a Secure Services Edge (SSE) solution. The combination of Axis’ SSE platform + HPE Aruba’s SD-WAN portfolio = SASE.
• Application Security: With the growth of APIs, open-source software, and cloud-native applications, application security has become critical. Capitalizing on this trend, Pathfinder invested in Cequence Security, an API lifecycle and security platform, last year (see our blog post announcement). While application security covers a broad range of solutions, another notable area is ASPM (e.g., ArmorCode, Apiiro, Bionic {acquired by CrowdStrike}), which goes beyond static code analysis to assesses vulnerabilities in production environments, in correlation with other applications.
• Cloud Security: As workloads move to the cloud, cloud security posture management (CSPM) and container workload security have become crucial. This segment overlaps the two above, but with additional capabilities that specialize it for the cloud (e.g., CSPM, monitoring & orchestration, threat intelligence, workload protection, and email protection).
• Identity & Access Management (IAM): IAM software enables the right individuals to access the right resources at the right times. It is an area that we believe will continue to grow as enterprises modernize their user-facing security solutions. ZTNA, as a framework, is utilized by most IAM solutions via multi-factor authentication (MFA), endpoint security, and privileged access management (PAM) to authenticate, authorize, and continuously validate users inside/outside a network.
• Data Security & Privacy: Statista estimates that 60%+ of all corporate data was stored in the cloud as of early 2022, up from 30% in 2015.⁴ As such, data security solutions have been trending towards cloud environments and data governance has become essential to comply with policies and regulations around cloud privacy. Recognizing the market demand, Pathfinder invested in Alation, a data governance and cataloging platform, and BigID, a data privacy and security platform.
• Endpoint Security: Cloud-native solutions for endpoint (i.e., device) security are on the rise, as management via the cloud allows the benefit of remote endpoint monitoring through a single agent that can apply policies broadly. Companies in this space develop detection and response, endpoint operations management, and threat hunting solutions.
• Security Operations: The popularity of “SecOps” is driven by the notion that it is no longer sufficient for risk management platforms to simply identify all IT resources; security teams also need to know how assets exist under different security postures and in correlation with each other. Included in this sector are managed detection and response (MDR) and eXtended Detection and Response (XDR) platforms, which utilize human operators and ML to correlate signals across Endpoint Security solutions.
GenAI, though still in its infancy, has reinvigorated the AI industry, but like any disruptive technology, it comes with its own unique security vulnerabilities. To this end, the OWASP (Open Worldwide Application Security Project)⁵ recently published “OWASP Top 10 for LLM Applications”, which highlights threats such as “Prompt Injections” that manipulate LLMs into performing unintended actions, “Model Denial of Service” attacks that degrade LLM performance, and “Supply Chain Vulnerabilities” associated with third-party data sets and pre-trained models.⁶ Turning these vulnerabilities into opportunities are early-stage companies building from the ground-up, such as Hidden Layer and Kindo, as well as more mature ventures layering on GenAI security capabilities, such as Robust Intelligence. Although companies focused on AI/ML security have existed for several years (both as ML-powered cybersecurity solutions and tooling to secure ML environments), the pervasive growth of GenAI is bringing the need for a well-defined AI Security sector to a tipping point. Pathfinder is actively tracking developments in GenAI-related security, and we expect our Cybersecurity Landscape to continue to evolve as these AI Security companies gain traction.
At a time when the attack surface is rapidly expanding across hybrid environments, corporate endpoints are traversing personal/professional boundaries, and GenAI is growing rampantly without meaningful regulation, Pathfinder intends to stay ahead of the curve. To that end, we aim to partner with startups that can help secure HPE GreenLake (core), HPE GreenLake for Large Language Models, and HPE Machine Learning Development Environment. If this resonates with you and you plan to fundraise for your company, please reach out to us!
²Forbes, Inc. "The Quest To Close The Cybersecurity Talent Gap." Oct. 16, 2023. forbes.com.
³PWC. "PwC Targets Managed Services Opportunity." Sept. 19, 2023. pwc.com.
⁵The Open Worldwide Application Security Project (OWASP, est. 2001) is one of world’s largest, most distinguished non-profit organizations concerned with software security.
⁶OWASP Foundation, Inc. “OWASP Top 10 for Large Language Model Applications.” Dec. 6, 2023. owasp.com
If you like this article consider subscribing to our bi-monthly newsletter to get information about our portfolio, solutions, and insights delivered to your inbox.